
In the dynamic digital landscape, the universality of cyber threats has never been more significant. This article searches into Cyber Security Managed Services, exploring their importance, key components, and benefits and dispelling common mistakes.
Importance of Cyber Security Managed Services
The significance of security-managed Managed Services lies in their pivotal role as proactive guardians against evolving digital threats. These services ensure continuous monitoring, ready detection, and robust protection mechanisms, protecting businesses from possible cyber-attacks.
Protecting Opposite Evolving Threats
The digital world is constantly evolving, and so are cyber menaces. Cyber Security Managed Services act as a shield, adapting to new threats and ensuring your systems remain safe. Shielding digital realms from ever-changing threats, the ‘Protecting Against Evolving Threats’ strategy within Cyber Security Managed Services needs adaptive measures, constant alertness, and cutting-edge technologies to secure systems against appearing cyber risks.
Proactive Monitoring and Detection
Instead of a reactive approach, these services provide proactive monitoring, detecting potential threats before they can cause harm. This level of alertness is crucial in the current cybersecurity landscape. Embracing an alertness stance, ‘Proactive Monitoring and Detection’ in Cyber Security Managed Services requires continuous surveillance and fast identification of potential threats. This proactive approach ensures swift responses, minimizing the impact of emerging cybersecurity risks.
Critical Components of Cyber Security Managed Services
At the core of Cyber Security Managed Services, the ‘Key Components’ encompass robust elements such as firewalls and Interruption of detection systems. These critical components and regular security audits form the backbone of comprehensive cybersecurity strategies and secure digital resilience.
Firewalls and Interruption Of Detection Systems
A robust cybersecurity strategy includes firewalls and Interruption of detection systems. Managed services implement and monitor these components to thwart unauthorized access. Acting as digital sentinels, ‘Firewalls and Intrusion Detection Systems’ form the frontline of Cyber Security Managed Services. Firewalls erect protective barriers, while Interruption of detection systems proactively identify and thwart unauthorized access, collectively fortifying digital environments against potential threats.
Regular Security Audits
Regular security audits are imperative for identifying vulnerabilities. Managed Security Services conducts thorough audits to fortify your digital infrastructure. Critical to cybersecurity integrity, ‘Regular Security Audits’ within Cyber Security Managed Services involve systematic assessments to identify vulnerabilities. These routine examinations ensure a proactive stance against potential threats, enhancing the overall strength and most vital of digital infrastructures.

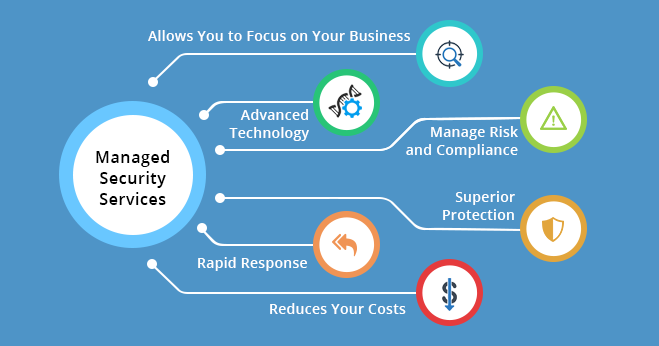
Benefits of Utilizing Managed Security Services
Realizing multifaceted advantages, the ‘Benefits of Utilizing Managed Security Services’ extend beyond cost-efficiency. Access to expert professionals and comprehensive protection against evolving threats make these services necessary, safeguarding businesses with modified and proactive cybersecurity solutions.
Cost-Efficiency
Contrary to popular belief, implementing managed security services can be cost-efficient. The expense of a potential cyber-attack far exceeds the investment in vital security measures. Within managed security services, ‘Cost efficiency’ signifies a strategic investment. Contrary to misconceptions, the expense is outweighed by the potential cost of cyber-attacks, making these services a prudent and economical choice for robust cybersecurity.
Access to Skilled Professionals
Engaging managed services provides access to a team of skilled cybersecurity professionals. This expertise is precious for businesses needing an in-house security team. Access to Skilled Professionals in managed security services ensures a reservoir of expertise at your fingertips. Businesses benefit from cybersecurity professionals’ combined knowledge and experience, more robust defences, and confidence in mitigating potential threats.
Common Misconceptions about Cyber Security Managed Services
Dispelling myths surrounding Cyber Security Managed Services, ‘Common Misconceptions’ include the belief that these services are exclusively for large enterprises or too expensive. In reality, they are tailored for businesses of all sizes and prove cost-effective, ensuring comprehensive cybersecurity.
Only for Large Enterprises
While significant acts commonly use managed security services, small and medium-sized businesses can benefit equally. Customized solutions are available to suit businesses of all sizes. The notion of Cyber Security Managed Services being ‘Only for Large Enterprises’ needs to be corrected. Tailored solutions accommodate companies of all sizes, deny the myth, and emphasize the availability and scalability of these vital cybersecurity services.
It’s Too Expensive
The cost of managed security services is a hint of the potential losses experienced from a cyber-attack. It’s an investment in the continuance and security of your business. Opposite to the belief that Cyber Security Managed Services are ‘Too Expensive,’ the reality is that a cost-effective investment is open. The amount pales in contrast to the potential financial losses experienced from cyber threats, making it a cautious and valuable security measure.
Choosing the Right Managed Security Services Providers
In cybersecurity, ‘Choosing the Right Managed Security Services Providers’ requires analyzing business needs and the provider’s regard. Optimal selection ensures tailored solutions, seamless integration, and a robust defence against evolving cyber threats.
Assessing Business Needs
Understanding your business’s unique security requirements is crucial in selecting the right managed security service provider. A tailored approach ensures optimal protection. Assessing business needs when choosing a managed security service provider is critical. Tailoring cybersecurity solutions to match the business’s unique requirements ensures optimal protection, making the assessment an integral part of the decision-making process.
Reputation and Experience
Researching the reputation and experience of potential providers is essential. Look for a provider with a proven course record in cybersecurity. Reputation and experience are paramount in selecting a Managed Security Service Provider. A provider’s track record and skill determine their ability to safeguard businesses effectively, making reputation and experience crucial factors in decision-making.
Real-Life Examples of Successful Implementation
Real-life examples of Successful Implementation’ showcase the tangible benefits of Managed Security Services. From transformative cybersecurity strategies to thwarting potential attacks, these examples provide concrete evidence of these services’ effectiveness and value to businesses.
Company A’s Cyber Security Transformation
Faced with persistent cyber threats, Company A implemented managed security services. The result? A significant reduction in successful attacks and enhanced overall security. Company A’s Cyber Security Transformation’ illustrates a real-world cybersecurity success story. Company A’s proactive engagement with Managed Security Services significantly reduced successful cyber attacks, showcasing the transformative power of robust cybersecurity measures.
Small Business B Avoids a Potential Cyber Attack
Small Business B proactively engaged in managed security services and thwarted a potential cyber attack. The investment proved invaluable in safeguarding their digital assets. Small Business B Avoids a Potential Cyber Attack’ exemplifies the impact of Managed Security Services on smaller enterprises. By proactively engaging these services, Small Business B successfully thwarted a potential cyber threat, highlighting these services’ invaluable protection.
Addressing Challenges in Implementing Managed Security Service
Addressing challenges related to Implementing Managed Security Services involves overcoming hurdles like employee resistance and seamless integration. Effective communication, training, and strategic integration solutions ensure a smooth transition, fostering a culture of cybersecurity within the organization.
Employee Resistance
Employees may need to be more familiar with new security measures. Effective communication and training can overcome this resistance, fostering a culture of cybersecurity. Employee Resistance’ to implementing Managed Security Services is a common challenge rooted in unfamiliarity. Overcoming this hurdle requires effective communication and training strategies, fostering an understanding of the importance and benefits of enhanced cybersecurity measures among employees.
Integration with Existing Systems
Integration challenges are expected. Choosing a provider that ensures the most substantial match integration with your existing systems is vital for a smooth transition. Integration with existing systems is a critical feature of applied managed security services. Ensuring seamless integration requires careful selection of a provider that aligns with the organization’s current basic structure, minimizing disruptions and maximizing the success of cybersecurity measures.

Future Trends in Cyber Security Managed Services
‘Future Trends in Cyber Security Managed Services’ signal progress like AI integration and zero-trust security models. These trends display the industry’s dedication to preventing apparent threats and ensuring dynamic, cutting-edge solutions for evolving cybersecurity opposition.
Artificial Intelligence and Machines Learning Integration
The integration of AI and machine learning increases threat detection capabilities. Managed services leveraging these technologies provide a proactive defence against evolving threats. Artificial Intelligence and Machines Learning Integration’ in Cyber Security Managed Services revolutionize menace detection. By controlling the power of AI and ML, these services proactively identify and neutralize evolving cyber threats, ensuring a dynamic and adaptive defence mechanism for businesses.
Zero Trust Security Models
The adoption of zero-trust security models is gaining momentum. These models assume no entity, inside or outside the organization, can be trusted, reinforcing overall security. Zero-trust security Models represent a paradigm shift in Cyber Security Managed Services. Operating on the principle of trust to verify, these models assume no entity, internal or external, can be trusted, fortifying overall security and minimizing potential vulnerabilities.
Tips for Individuals to Enhance Personal Cyber Security
Tips for Individuals to Enhance Personal Cyber Security emphasize practical measures. Implementing strong password practices and regular software updates are fundamental steps, empowering individuals to contribute to their cybersecurity in today’s digital landscape actively.
Strong Password Practices
Individuals play a crucial role in cybersecurity. Strong password practices are a simple and effective way to increase secret security. ‘Strong Password Practices’ involve creating and maintaining strong passwords. This simple yet effective approach increases personal cybersecurity by fortifying digital accounts against unauthorized access, providing an essential layer of protection in the interconnected online world.
Regular Software Updates
Although software updates are often overlooked, they are a fundamental step in closing potential security loopholes. Regular Software Updates are foundational to personal cybersecurity. Consistently updating software verifies that the latest security patches are applied, closing possible defects and safeguarding against evolving threats, contributing to an energetic defence scheme for individuals.

The Role of Managed Security Service in Compliance
The Role of Managed Security Services in Compliance underlines their importance in attaching to regulations like GDPR. These services ensure businesses meet data protection standards and industry-specific compliances and display a commitment to legal and social cybersecurity practices.
GDPR Data Protection
Industry-Specific Compliance
Different industries have unique compliance requirements. Managed security services tailor their approach to ensure adherence to industry-specific regulations. Industry-specific compliance within Managed Security Services focuses on tailoring cybersecurity measures to meet specific industry regulations. This targeted approach ensures businesses adhere to unique standards, address sector-specific cybersecurity challenges, and demonstrate a commitment to regulatory compliance.

Conclusion
Cyber menaces are inevitable in a world dominated by digital interactions. Cyber Security Managed Services appear as intense matches of protection, offering dynamic solutions, expertise, and versatility. Financing these services is an investment in the long-term security and sustainability of your digital advantage.
What is a managed services example?
These services may include network and infrastructure management, security and monitoring. Most MSPs bill an upfront setup or transition fee and an ongoing flat or near-fixed monthly payment, which provides clients with predictable IT support costs.
Why do I need managed services?
Managed Services, provided by an experienced Managed Services Provider, can help organizations focus on their core objectives, get access to the skills and expertise they need, optimize operating expenses, enable seamless scalability, and avoid costly downtime – all while







