Cybersecurity risk assessment are vital processes for safeguarding digital assets from potential threats. They comprehensively evaluate systems, networks, and data to identify vulnerabilities and potential risks. Organizations can prioritize their security efforts and allocate resources effectively by conducting thorough assessments.
These assessments help understand the potential impact of cyber threats on business operations, data integrity, and customer trust. Moreover, cybersecurity risk assessment aids in compliance with regulatory requirements and industry standards, ensuring that organizations adhere to best practices in information security.
They also empower organizations to address emerging threats and strengthen their overall security posture proactively. Regular cybersecurity risk assessments are essential for maintaining resilience against evolving cyber threats in today’s interconnected digital landscape.
Cybersecurity Risk Assessment
Welcome to Cybersecurity risk assessment, which is pivotal for understanding the landscape of digital security threats. It systematically evaluates potential risks and vulnerabilities within an organization’s information systems. Cybersecurity risk assessment identifies, analyzes, and prioritizes risks to sensitive data, critical infrastructure, and operational continuity.
Organizations can develop proactive strategies to mitigate potential cyber threats by comprehensively assessing the threat landscape. Understanding the importance of cybersecurity risk assessment enables businesses to allocate resources efficiently, implement robust security measures, and maintain regulatory compliance.
As cyber threats evolve in complexity and sophistication, a solid foundation in cybersecurity risk assessment is essential for safeguarding against potential breaches and protecting valuable assets from unauthorized access and exploitation.

Understanding the Importance of Cybersecurity
Understanding the importance of cybersecurity is crucial in today’s digital age, where sensitive information is constantly at risk of unauthorized access and exploitation. Cybersecurity protects personal data, financial assets, and critical infrastructure from malicious attacks and threats.
It plays a vital role in safeguarding individuals, businesses, and governments against cybercrime, data breaches, and identity theft. Moreover, cybersecurity fosters trust and confidence in online transactions, digital communications, and information sharing. Organizations can mitigate potential risks by prioritizing cybersecurity measures, upholding data integrity, and preserving their reputation in the face of evolving threats.
Emphasizing the importance of cybersecurity underscores the need for continuous vigilance, proactive measures, and investments in advanced technologies to combat cyber threats effectively and ensure a secure digital environment for all.
What is a cybersecurity risk assessment?
A cybersecurity risk assessment is a comprehensive process to identify, analyze, and mitigate potential threats and vulnerabilities within an organization’s digital infrastructure. It involves evaluating cyber threats’ likelihood and potential impact on sensitive data, critical systems, and operational continuity.
By systematically assessing the threat landscape, organizations can prioritize security measures, allocate resources effectively, and implement controls to manage and mitigate identified risks. Cybersecurity risk assessments are crucial in enhancing overall security posture, regulatory compliance, and resilience against evolving cyber threats in today’s interconnected digital landscape.
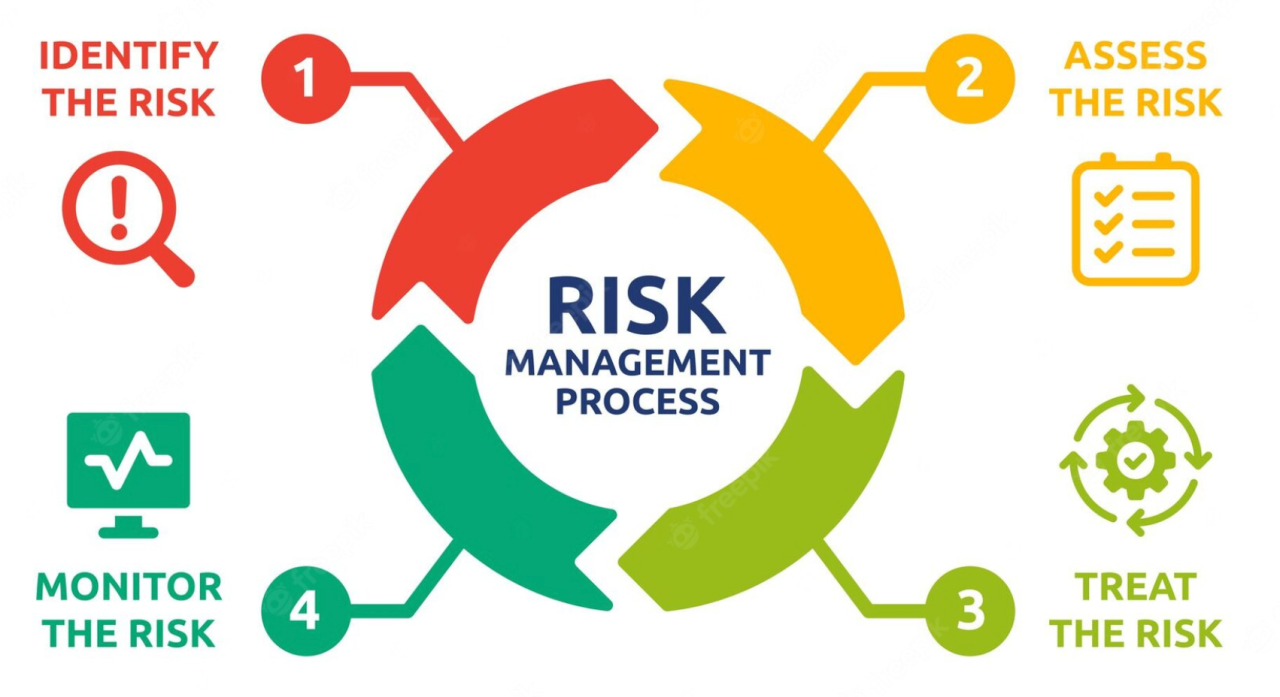
The Process of Cybersecurity Risk Assessment
Cybersecurity risk assessment involves systematically identifying, analyzing, and mitigating potential threats and vulnerabilities in an organization’s digital infrastructure. It includes asset identification, threat analysis, vulnerability assessment, risk evaluation, and implementing controls to effectively manage and mitigate identified risks.
Identification of Assets and Threats
Identification of assets and threats is a crucial phase in cybersecurity risk assessment. It involves identifying all digital assets within an organization’s infrastructure, including hardware, software, data repositories, and personnel.
Simultaneously, malware, phishing attacks, and insider threats are assessed to understand potential risks. Asset identification helps prioritize resources and focus security efforts where they are most needed. By comprehensively identifying assets and threats, organizations can understand their risk landscape and tailor their cybersecurity strategies accordingly.
This phase lays the foundation for subsequent steps in the risk assessment process, including vulnerability analysis and risk evaluation, enabling organizations to safeguard their critical assets effectively against potential cyber threats.
Analysis of Vulnerabilities
The analysis of vulnerabilities is a critical component of cybersecurity risk assessment. It systematically examines potential weaknesses and security flaws within an organization’s digital infrastructure. Vulnerabilities include outdated software, misconfigured systems, weak passwords, and inadequate access controls.
Through thorough analysis, organizations can identify areas of potential exploitation by cyber threats. This phase often involves using vulnerability scanners, penetration testing tools, and security audits to uncover weaknesses and assess their risk level.
Organizations can prioritize remediation efforts by understanding vulnerabilities and implementing appropriate security controls to mitigate risks effectively. Analysis of vulnerabilities forms a foundational step in enhancing overall cybersecurity resilience and protecting sensitive data and critical assets from unauthorized access and exploitation.
Evaluation of Risks
The evaluation of risks is a pivotal stage in cybersecurity risk assessment. It involves assessing the likelihood and potential impact of identified vulnerabilities and threats on an organization’s digital assets and operations. Risks are categorized based on their severity and prioritized for mitigation. By evaluating risks, organizations can make informed decisions regarding resource allocation and implement controls to manage and reduce their overall cyber risk exposure effectively.

Implementation of Controls
Controls and countermeasures are implemented to reduce risks after identifying, analyzing, and evaluating them. The implementation of controls is a crucial phase in cybersecurity risk assessment. It involves deploying security measures and countermeasures to mitigate identified risks and vulnerabilities within an organization’s digital infrastructure.
This phase encompasses deploying technical solutions such as firewalls, intrusion detection systems, encryption protocols, and security patches and implementing policies, procedures, and security awareness training programs. By effectively implementing controls, organizations can strengthen their security posture and minimize the likelihood and impact of cyber threats.
Types of Cybersecurity Risks
Cybersecurity risks can be classified into external and internal threats. External threats originate from outside the organization, such as hackers, cybercriminals, and nation-state actors, while internal threats arise from employees, contractors, or partners with malicious intent or unintentional actions.
Benefits of Cybersecurity Risk Assessment
- Proactive identification and mitigation of potential risks
- Protection of sensitive data and critical assets
- Compliance with regulatory requirements and industry standards
- Preservation of organizational reputation and customer trust
Common Challenges in Cybersecurity Risk Assessment
Challenges in cybersecurity risk assessment include the complexity of IT environments, the evolving threat landscape, resource constraints, and a need for cybersecurity expertise. Additionally, organizations may need help prioritizing risks and achieving buy-in from stakeholders.
Best Practices for Cybersecurity Risk Assessment
- Conduct regular risk assessments and updates to adapt to changing threats.
- Foster a culture of cybersecurity awareness and accountability across the organization.
- Implement a layered defense strategy with multiple security controls and redundancies.
- Engage external cybersecurity experts and leverage threat intelligence for insights into emerging threats.
Tools and Technologies for Cybersecurity Risk Assessment
Various tools and technologies facilitate cybersecurity risk assessment, including vulnerability scanners, penetration testing tools, security information and event management (SIEM) systems, and risk management platforms.

Compliance and Regulations in Cybersecurity
Compliance and regulations in cybersecurity are essential for organizations to adhere to industry standards and legal requirements regarding data protection and information security. Regulations such as GDPR, HIPAA, PCI DSS, and NIST frameworks outline guidelines for safeguarding sensitive information, ensuring privacy, and mitigating cybersecurity risks.
Compliance with these regulations helps organizations avoid legal liabilities, financial penalties, and reputational damage from data breaches or non-compliance. Maintaining compliance demonstrates a commitment to protecting customer data and trust in a digital landscape.
The Role of AI and Machine Learning in Cybersecurity Risk Assessment
The role of AI and machine learning in cybersecurity risk assessment is becoming increasingly prominent in the digital landscape. These technologies empower organizations to enhance threat detection, analysis, and response capabilities. AI algorithms can analyze vast amounts of data to identify patterns and anomalies, enabling proactive threat prevention and incident response.
Machine learning algorithms can also adapt and evolve based on new data and emerging threats, improving the accuracy and effectiveness of cybersecurity measures over time. By leveraging AI and machine learning, organizations can augment human capabilities, automate routine tasks, and stay ahead of evolving cyber threats, enhancing their overall cybersecurity posture and resilience in the face of increasingly sophisticated attacks.
Case Studies
Equifax Data Breach: In 2017, Equifax suffered a massive data breach, exposing sensitive information about 147 million individuals.
Wanna Cry Ransomware Attack: The Wanna Cry ransomware attack in 2017 infected over 200,000 computers worldwide, exploiting a vulnerability in Microsoft Windows systems.
SolarWinds Supply Chain Attack: In 2020, SolarWinds experienced a sophisticated supply chain attack, compromising numerous organizations through compromised software updates.
Future Trends in Cybersecurity Risk Assessment
Future trends in cybersecurity risk assessment include the integration of artificial intelligence, machine learning, and automation for threat prediction and prevention, the adoption of zero-trust security models, and the rise of quantum-resistant encryption algorithms.

Conclusion
In conclusion, cybersecurity risk assessment is an indispensable process for organizations to identify, analyze, and mitigate potential threats to their digital infrastructure. Organizations prioritize resources and implement security measures to protect sensitive data and critical operations.
Compliance with regulatory standards and industry best practices ensures adherence to legal requirements and enhances stakeholder trust. As cyber threats continue to evolve, proactive risk assessment and mitigation strategies are paramount for maintaining resilience against emerging threats. Prioritizing cybersecurity safeguards assets upholds data integrity, and preserves reputation.
How often should organizations conduct cybersecurity risk assessments?
Organizations should conduct cybersecurity risk assessments regularly, at least annually, or whenever significant changes occur in the IT environment, such as system upgrades, acquisitions, or regulatory changes.
What are some common challenges organizations face in cybersecurity risk assessment?
Common challenges include the complexity of IT environments, resource constraints, lack of cybersecurity expertise, and evolving threat landscape.
What role do regulations and compliance standards play in cybersecurity risk assessment?
Regulations and compliance standards provide guidelines and requirements for protecting sensitive data, ensuring privacy, and mitigating cybersecurity risks. Compliance helps organizations avoid legal liabilities and reputational damage.
How can AI and machine learning enhance cybersecurity risk assessment?
AI and machine learning technologies can automate threat detection, analyze vast amounts of data to identify patterns and anomalies and enhance incident response capabilities by providing real-time insights into emerging threats.