
Network Security Vulnerability Assessment
Safeguarding Your Digital Infrastructure
In today’s interconnected world, where digital interactions are paramount, network security vulnerability assessment is critical to fortifying the integrity of digital infrastructure. With digital dangers developing alarmingly, understanding organizational weaknesses is fundamental for organizations and people. This extensive guide dives into the complexities of organization security weakness evaluation, enabling you to support your guards against possible breaks.
Understanding Network Security Vulnerability Assessment
Understanding Network Security vulnerability Assessment is vital to building advanced foundations against digital dangers. This interaction includes methodically distinguishing, examining, and alleviating weaknesses inside network parts.
By analyzing equipment, programming, arrangements, and client rehearsals, associations can pinpoint potential shortcomings that vindictive entertainers could exploit. A proactive appraisal is essential, empowering organizations to address weaknesses before use. Network security weakness evaluation includes the revelation stage, weakness checking, risk appraisal, and entrance testing.
Associations can upgrade their security posture and limit the risk of information breaches through powerful weaknesses in their executive practices like fixing the board, nonstop observing, and representative preparation. Understanding the subtleties of organization security weakness appraisal enables organizations to remain in front of developing digital dangers and shield their computerized resources.
The Importance of Proactive Assessment
The importance of proactive assessment in network security cannot be overstated. As opposed to hanging tight for security breaks to happen, associations should take on a preplanned position by leading standard weakness evaluations.
Proactive evaluation empowers organizations to recognize and address weaknesses before digital aggressors exploit them. By avoiding likely dangers, associations can limit the risk of information breaks, monetary misfortunes, and reputational harm. Proactive evaluation additionally permits focusing on remediation endeavors, guaranteeing fundamental weaknesses are addressed quickly.
Eventually, embracing an aggressive way to deal with network security weakness evaluation improves an association’s versatility against developing digital dangers and fortifies its general security act in an undeniably computerized scene.

Key Components of Network Security Vulnerability Assessment
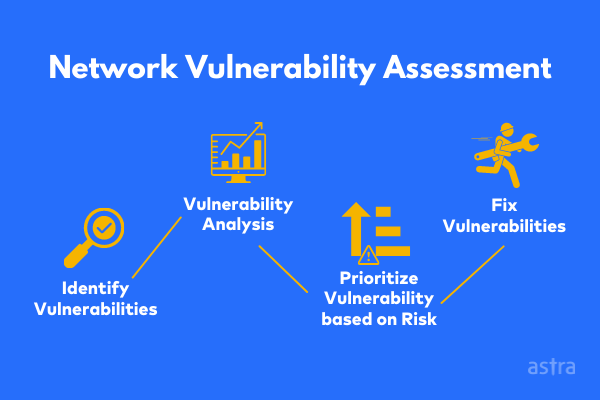
Critical components of network security vulnerability assessment encompass several crucial steps. Right off the bat, the disclosure stage includes distinguishing gadgets and frameworks inside the organization through complete filtering and planning strategies.
Furthermore, entrance testing, or moral hacking, reproduces genuine world digital assaults to survey existing security controls and recognize exploitable weaknesses. By carrying out these essential parts, associations can proactively identify and moderate weaknesses within their organization’s foundation, improving their general security act and limiting the risk of digital dangers and information breaches.
Discovery Phase
The discovery phase is a critical component of network security vulnerability assessment. It includes methodically recognizing gadgets and frameworks inside the organization and utilizing thorough examination and planning procedures.
During this stage, security experts learn about the organization’s design, including all open passage focuses and expected weaknesses. Through careful revelation, associations can determine the extent of their organizational framework and focus on the ensuing weakness evaluation exercises.
By outlining the corporate scene, organizations can proactively distinguish potential security dangers and take preventive measures to relieve them. The disclosure stage establishes an exhaustive weakness evaluation technique, empowering associations to reinforce their protections and defend against potential digital dangers and breaks.
Vulnerability Scanning
Vulnerability scanning plays a pivotal role in network security vulnerability assessment. It includes utilizing particular apparatuses and programming to efficiently distinguish known weaknesses and misconfigurations across network gadgets and applications.
Associations can proactively determine potential shortcomings that digital aggressors could exploit by leading weakness filters. These sweeps give essential knowledge into the organization’s security posture, permitting organizations to focus on remediation endeavors and assign assets.
Weakness filtering is vital for proactive safety efforts, empowering associations to avoid rising dangers and limiting the risk of information breaches and digital assaults. By utilizing vulnerability filtering devices, organizations can improve their general security posture and keep up with the honesty of their advanced resources.

Risk Assessment
Risk assessment is a crucial step in network security vulnerability assessment. It includes assessing the seriousness and expected effect of recognized weaknesses within an organization’s foundation. Through meticulous examination, associations can assign risk scores to weaknesses, focusing on remediation endeavors in light of their present danger.
Organizations gain essential insights into the failings representing the central gamble in their activities and delicate information by leading gamble evaluations. This empowers them to designate assets successfully and carry out assigned safety efforts to relieve likely dangers.
Risk evaluation is a proactive way to deal with online protection. It permits associations to avoid developing dangers and defend their computerized resources against unapproved access and double-dealing.
Penetration Testing
Penetration testing, or ethical hacking, is pivotal to network security vulnerability assessment. It includes mimicking genuine world digital assaults to assess the viability of existing security controls and distinguish expected weaknesses within an organization framework.
By directing infiltration tests, associations can reveal and address exploitable shortcomings before malignant entertainers take advantage of them. Infiltration testing goes beyond mechanized weakness-checking by utilizing human aptitude to reproduce complex assault situations.
This active methodology gives essential knowledge about the flexibility of the association’s protections and distinguishes holes in its security posture. By embracing entrance testing as a component of their network protection system, organizations can proactively moderate dangers and upgrade the general strength of their computerized foundation.

Implementing Effective Vulnerability Management
Implementing effective vulnerability management is paramount to maintaining robust network security. It includes laying out proactive measures to recognize, evaluate, and alleviate weaknesses within the organization’s foundation.
The ideal fix for executives is pivotal, guaranteeing that product and firmware weaknesses are instantly tended to through updates and fixes. Ceaseless checking permits associations to progressively recognize and answer security episodes, limiting likely harm and unapproved access. Employee training and awareness programs are crucial for fostering a culture of cybersecurity within organizations.
By executing these procedures, organizations can reinforce their security posture, limit the risk of information breaches, and defend sensitive data from digital dangers. A successful weakness for executives is a continuous cycle that requires joint effort, carefulness, and a guarantee of proactive security rehearsals.
Patch Management
Patch management is a critical aspect of effective cybersecurity practices. It includes the convenient use of updates and fixes to programming and firmware to address known weaknesses and security shortcomings. Staying updated helps organizations minimize risks from malicious actors exploiting vulnerabilities.
Continuous Monitoring
Continuous monitoring is a vital practice for maintaining robust network security. It includes ceaselessly surveilling network exercises, frameworks, and information to distinguish and answer constant security dangers. Continuous monitoring helps identify suspicious behaviors and potential security breaches in real-time.
Employee Training and Awareness
Employee training and awareness are pivotal in bolstering overall cybersecurity within organizations. By providing extensive preparation programs, organizations can teach workers about potential security dangers, best practices for information assurance, and the significance of sticking to security approaches and methodologies.
This preparation engages workers to perceive and report dubious exercises, phishing endeavors, and other security gambles, lessening the probability of effective digital assaults. Moreover, cultivating a culture of safety mindfulness urges workers to take responsibility for obligations and effectively add to the association’s guard against dangers. Regular training, simulated phishing exercises, and ongoing communication ensure employee readiness for cybersecurity defense.

Benefits of Network Security Vulnerability Assessment
Investing in network security vulnerability assessments offers numerous benefits to organizations of all sizes.
Proactive Risk Management: Organizations can mitigate risks and prevent potential security breaches by identifying vulnerabilities before they are exploited.
Compliance Requirements: Many regulatory standards and industry frameworks mandate regular vulnerability assessments as part of compliance efforts.
Enhanced Security Posture: Vulnerability assessments enable organizations to strengthen their security posture and build resilience against evolving cyber threats.
Cost Savings: Proactively addressing vulnerabilities reduces the potential costs associated with data breaches, legal liabilities, and reputational damage.
Conclusion
Network security weakness evaluation is a principal part of online protection and safeguarding strategies in computerized development and networks. By proactively distinguishing and relieving weaknesses inside the organization’s foundation, associations can shield touchy information, save client trust, and maintain functional progression despite developing digital dangers.
Embracing a comprehensive way to deal with weakness, the executives engage associations to remain one stride in front of foes, strengthen their computerized safeguards, and protect the trustworthiness of their automated resources. In the evolving online protection scene, network security vulnerability assessment is crucial.
Why is Network Security Vulnerability Assessment critical?
Network Security Vulnerability Assessment is essential because it allows organizations to proactively identify and address vulnerabilities before malicious actors exploit them. By conducting regular assessments, businesses can minimize the risk of data breaches, financial losses, and reputational damage by strengthening their digital defenses and staying ahead of emerging threats.
How is Network Security Vulnerability Assessment conducted?
Network Security Vulnerability Assessment involves several key steps, including the discovery phase, vulnerability scanning, risk assessment, and penetration testing. Automated tools and manual techniques identify and prioritize vulnerabilities based on their severity and potential impact.
What are the benefits of Network Security Vulnerability Assessment?
The benefits of Network Security Vulnerability Assessment include enhancing security posture, minimizing the risk of cyber threats, and preserving the integrity of digital assets. It helps organizations comply with regulatory requirements and proactively address vulnerabilities to protect sensitive information.
How often should Network Security Vulnerability Assessment be performed?
The frequency of Network Security Vulnerability Assessment depends on factors such as the size of the network, industry regulations, and the evolving threat landscape. Generally, assessments should be conducted regularly, ideally quarterly or biannually, to ensure continuous protection against emerging threats and maintain operational resilience.








