
Understanding Asymmetric Encryption
Introduction
In the advanced world, asymmetric encryption. Whether you’re making a web-based exchange, sending arranged messages, or getting data, encryption accepts a fundamental part. Among the different encryption procedures, topsy-turvy encryption stands out as perhaps the most dependable technique. Yet, what’s going on here? How can it function? Also, for what reason is it so essential to current network safety? We should plunge profoundly into the universe of unbalanced encryption.
What is hilter-kilter encryption?
Uneven encryption, otherwise called public-key cryptography, is a system for scrambling data using two free, but mathematically related, keys: a public key and a classified key. Rather than symmetric encryption, where a comparable key is used for encryption and unscrambling, topsy-turvy encryption keeps the cycle more secure by using two specific keys.
How Does Asymmetric Encryption Work?
- Key Generation: A pair of keys (public and private) is generated.
- Encryption: The sender encrypts the message using the recipient’s public key.
- Transmission: The encrypted message is sent over the network.
- Decryption: The recipient uses their private key to decrypt the message.
Since the private key is never shared, even if the public key is intercepted, the data remains secure.
Key Components of Asymmetric Encryption
1. Public Key
- Available to anyone.
- Used for encrypting data.
2. Private Key
- Kept secret by the owner.
- Used for decrypting data.
3. Algorithms
Regularly utilized unbalanced encryption algorithms include:
- RSA (Rivest-Shamir-Adleman)
- ECC (Elliptic Curve Cryptography)
- DSA (Digital Signature Algorithm)
Why use asymmetric encryption?
1. Enhanced Security
In contrast to symmetric encryption, regardless of whether an aggressor gets hold of the public key, they can’t unscramble messages without the confidential key.
2. Digital Signatures
Uneven encryption empowers advanced marks, confirming the shipper’s genuineness and guaranteeing message respectability.
3. Secure Key Exchange
Since symmetric encryption requires key trade, it is defenseless against block attempts. Hilter-kilter encryption dispenses with this gamble.
Applications of Asymmetric Encryption
1. SSL/TLS in Web Security
Secure Attachments Layer (SSL) and Transport Layer Security (TLS) depend on lopsided encryption to lay out secure associations over the web.
2. Email Encryption
Protocols like PGP (Pretty Good Privacy) use asymmetric encryption to secure email communication.
3. Cryptocurrency Transactions
Bitcoin and other cryptocurrencies use asymmetric encryption to secure transactions and digital wallets.
4. Secure Messaging
Applications like WhatsApp and Signal use unbalanced encryption to guarantee start-to-finish encryption for messages.
Benefits and Weaknesses of Asymmetric Encryption
🔐 1. Enhanced Security
Since uneven encryption utilizes two different keys, it kills the need to share a mystery key over possibly uncertain channels, decreasing the gamble of key splitting the difference.
🌎 2. Ideal for Secure Communication Over Public Networks
It allows secure data transmission over the internet, making it widely used in SSL/TLS protocols for web security and email encryption (e.g., PGP encryption).
✅ 3. Digital Signatures & Authentication
It enables digital signatures, ensuring data integrity and authenticity. This is critical for verifying the sender’s identity and preventing tampering.
🔑 4. Key Distribution is Safer
Unlike symmetric encryption, where securely sharing the secret key is a challenge, asymmetric encryption only requires public keys to be shared openly, while private keys remain confidential.
🔄 5. Supports Non-Repudiation
Since only the private key owner can generate a digital signature, asymmetric encryption prevents users from denying actions they performed (such as signing a document).
Weaknesses of Asymmetric Encryption
🐢 1. Slower Performance
Unbalanced encryption is computationally escalated, making it altogether slower than symmetric encryption. This makes it less commonsense for encoding enormous volumes of information.
🔑 2. Private Key Protection is Critical
On the off chance that the confidential key is lost or taken, scrambled information becomes difficult to reach or compromised. It’s basically impossible to recuperate lost information without the confidential key.
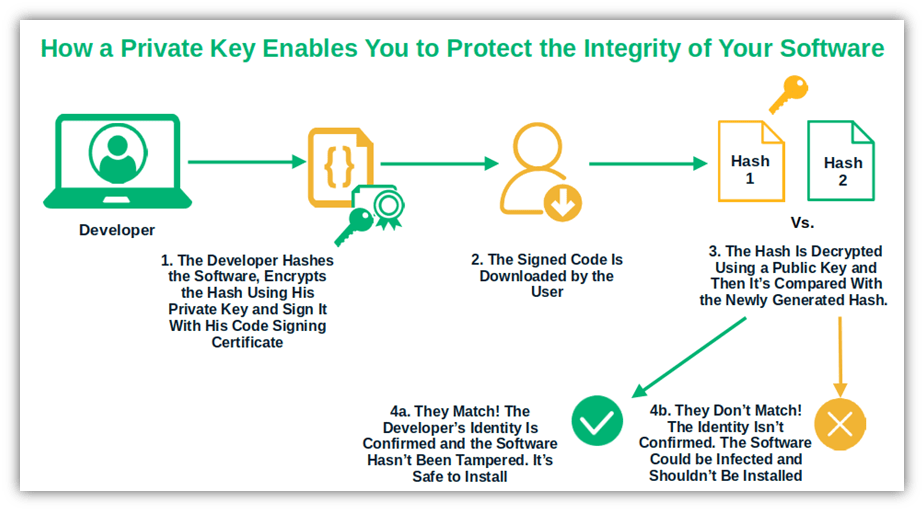
⚖️ 3. Key Management Can Be Complex
Managing multiple key pairs across different users and systems requires robust key management strategies, which can be complicated and costly.
🔓 4. Vulnerability to Man-in-the-Middle (MITM) Attacks
In the event that an aggressor captures and replaces a public key with their own, they could unscramble and modify messages prior to sending them. For this reason, testament specialists (CAs) are critical for confirming characters.
🛠️ 5. Hybrid Implementation is Often Needed
As a result of its shortcoming for mass information encryption, lopsided encryption is many times utilized close by symmetric encryption (e.g., in SSL/TLS, where uneven encryption is utilized for key trade and symmetric encryption gets the information).
How Asymmetric Encryption Differs from Symmetric Encryption
| Feature | Asymmetric Encryption | Symmetric Encryption |
|---|---|---|
| Keys | Uses a pair (public & private) | Uses a single key |
| Security | More secure | Less secure |
| Speed | Slower | Faster |
| Common Usage | SSL/TLS, Digital Signatures | File encryption, VPNs |
How to Implement Asymmetric Encryption
1. Generate Key Pair
Use tools like OpenSSL to generate a public-private key pair.
openssl genpkey -algorithm RSA -out private_key.pem
openssl rsa -pubout -in private_key.pem -out public_key.pem2. Encrypt a Message
openssl rsautl -encrypt -inkey public_key.pem -pubin -in message.txt -out encrypted.txt3. Decrypt the Message
openssl rsautl -decrypt -inkey private_key.pem -in encrypted.txt -out decrypted.txtConclusion
Asymmetric encryption is the foundation of current online cybersecurity. With its remarkable double-key component, it guarantees secure correspondences, validates characters, and safeguards delicate information. However it accompanies the computational above, the advantages far offset the disadvantages. Whether you’re perusing safely, sending encoded messages, or making digital money exchanges, uneven encryption is working in the background to protect your information.
What's the contrast among RSA and ECC encryption?
RSA depends on the trouble of figuring huge indivisible numbers, though ECC depends on elliptic bend science, offering similar security with more modest key sizes.
Might I at any point involve asymmetric encryption for document encryption?
It's conceivable yet wasteful. Regularly, unbalanced encryption is utilized to scramble a symmetric key, which is then utilized for record encryption.







