In today’s digital age, protecting web applications from cyber threats is paramount. With the increasing sophistication of web exploits, it is essential to have robust security measures in place. AWS Web Application Firewall (WAF) is a powerful tool designed to safeguard web applications from a variety of cyber threats, including SQL injection, cross-site scripting (XSS), and Distributed Denial-of-Service (DDoS) attacks.
Whether you’re a beginner or an experienced user, you’ll find valuable insights and practical advice on leveraging AWS WAF to enhance your web application’s security. By the end of this blog, you will have a solid understanding of AWS WAF, how it can protect your web applications from various threats, and the steps to implement it effectively in your security strategy.
What is AWS WAF?
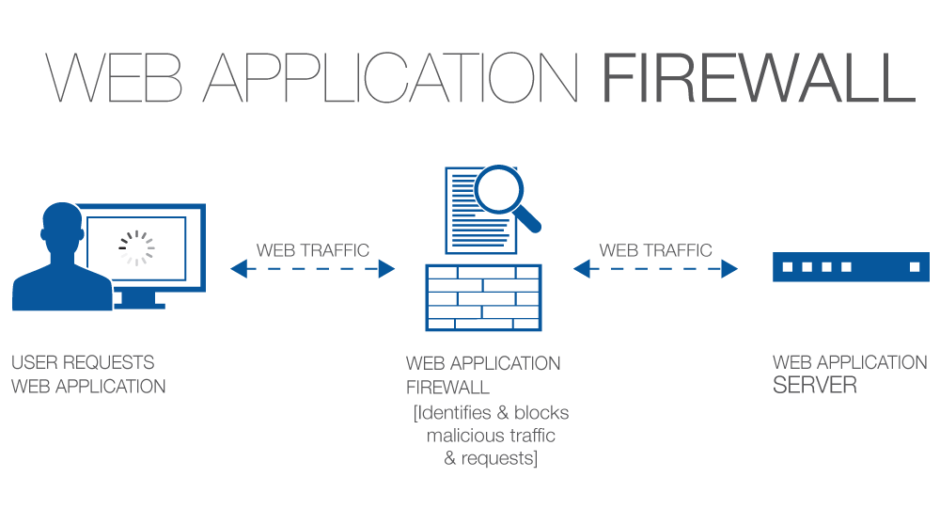
AWS WAF (Web Application Firewall) is a cloud-based security service provided by Amazon Web Services (AWS). It helps protect web applications from various types of attacks, such as SQL injection, cross-site scripting (XSS), and distributed denial of service (DDoS) attacks.
AWS WAF helps you manage and control your content by using IP addresses from where requests originate. Three key components make AWS WAF effective: Access Control Lists (ACL), Rules, and Rule Groups. Additionally, AWS WAF manages Web ACL capacity units (WCU) for rules, rule groups, and web ACLs. It includes a full-featured API to automate the creation, deployment, and maintenance of security rules.
Key Features
- Protection Against Common Attacks: AWS WAF protects against SQL injection, cross-site scripting (XSS), and other common web exploits.
- Customizable Rules: You can create custom rules that filter out specific traffic patterns.
- Scalability: AWS WAF scales automatically with your traffic.
AWS Web Application Firewall (WAF) Offers Protection from Common Web Exploits at Which Layer?
AWS WAF operates at the application layer (Layer 7) of the OSI model. This is crucial because most web-based attacks, such as SQL injection, cross-site scripting (XSS), and other common exploits, target the application layer. By filtering and monitoring HTTP and HTTPS requests, AWS WAF can inspect the content of the HTTP and HTTPS requests, making it highly effective at identifying and mitigating web-based attacks.
What is WAF in AWS and Can AWS WAF be integrated with other AWS services for a good security solution?
Furthermore, you can use AWS WAF logs to gain valuable insights into your application’s traffic and integrate them with services like Amazon Cloud Watch, Application Load Balancer (ALB), API Gateway and AWS Lambda for advanced monitoring and automated response.
Additionally, integrating AWS WAF with AWS Firewall Manager allows you to centrally manage and deploy firewall rules across multiple AWS accounts and resources. By combining AWS WAF with other AWS services, you can establish a robust and comprehensive security solution tailored to your specific needs.

How to Get AWS WAF
Before getting started with AWS WAF, ensure you have:
- An AWS account
- Basic understanding of AWS services like CloudFront, ALB, or API Gateway
Steps to Get AWS WAF
- Sign in to the AWS Management Console: Navigate to the WAF & Shield service.
- Create a Web ACL: A Web Access Control List (Web ACL) is a set of rules that define how AWS WAF inspects and filters web requests.
- Add Rules to the Web ACL: You can use predefined rules (managed rule groups) or create custom rules.
- Associate the Web ACL with Resources: Attach the Web ACL to your CloudFront distribution, ALB, or API Gateway stage.
How to Run AWS WAF
Running AWS WAF involves continuous monitoring and updating of rules to ensure optimal protection. Here’s how you can effectively run AWS WAF:
- Monitor Traffic: Use AWS WAF’s logging and metrics to monitor traffic patterns and identify potential threats.
- Update Rules: Regularly update your rules to adapt to new threats.
- Automate Response: Implement automation for common actions like blocking IPs after a certain threshold of malicious activity.
How Does AWS WAF Work? / Technical Workflow
AWS WAF protects web applications from malicious attacks through several key steps, ensuring security and effective threat management.
1. AWS Firewall Manager
AWS Firewall Manager allows centralized configuration and management of firewall rules across your AWS accounts and applications, simplifying the administration of multiple AWS WAF deployments.
2. AWS WAF
AWS WAF evaluates incoming traffic against specified rules to protect applications from common web exploits like SQL injection and cross-site scripting (XSS), allowing, blocking, or counting requests based on these rules.
3. Create a Policy
Using the visual rule builder in AWS WAF, you can create security policies that define how web traffic should be handled, preventing malicious requests from reaching your applications.
4. Block Filter
Block filters provide additional protection against known exploits and vulnerabilities by specifying conditions under which traffic should be blocked, such as specific IP addresses or request patterns.
5. Monitor
AWS WAF integrates with Amazon Cloud Watch to monitor web traffic and the effectiveness of your rules, providing metrics on incoming traffic. Amazon Kinesis Firehose can capture detailed request logs for further analysis, helping you fine-tune rules for enhanced security and performance.

Rule Types
- IP Match Conditions: Block or allow requests based on IP addresses.
- String Match Conditions: Inspect specific strings in request headers, cookies, or body.
- Size Constraint Conditions: Filter requests based on the size of specific parts of the request.
How to Use AWS WAF
- Use Managed Rules: AWS provides managed rule groups for common threats, saving you time and ensuring up-to-date protection.
- Create Custom Rules: Tailor your security by creating custom rules that address specific needs of your application.
- Regularly Review Logs: Use AWS WAF logs to review and understand the traffic patterns and refine your rules.
- Monitoring: Request details, then tune rules based on metrics and log data.
Getting Started with AWS WAF
AWS WAF monitors all web incoming and outgoing requests that are forwarded to API Gateway, Amazon Cloud Front, and Application Load Balancer. Here’s how you can get started with AWS WAF and create a Web ACL (Access Control List):
Step 1: Create a Web ACL
First, sign up for an AWS account, then go to the AWS Console and search for Web Application Firewall. You will land on the WAF home page. Choose “Create Web ACL.”
Step 2: Give a Name
Type the name you want to use to identify this Web ACL. Optionally, enter a description, and then hit “Next.”
Step 3: Add an AWS Managed Rules Rule Group
Add rules and rule groups by clicking on “Add managed rule groups.” AWS Managed Rules provides a collection of managed rule groups, most of which are free for AWS WAF users. After adding the managed rule group, choose to save the rule.
Creating Specific Rules
- Regular Rule: Protects the application from SQL injection attacks by checking if the URI path contains an SQL injection.
- Rate-based Rule: Blocks requests made from the same IP address after they exceed a certain limit in a specific time period.
Step 4: Configure Cloud Watch Metrics
Set up Cloud Watch metrics to monitor the incoming traffic and configure Amazon Kinesis Firehose for detailed request logs.
Step 5: Review Web ACL Configuration
In the final step, review all the rules and managed groups, then hit “Create Web ACL.” You will receive a confirmation message indicating that you have successfully created the Web ACL.

How to Setup AWS WAF
Setting up AWS WAF involves fine-tuning your configurations to ensure optimal protection. Follow these steps to set up AWS WAF effectively:
1. Web ACL Configuration:
- Define the default action (allow or block).
- Organize rules into rule groups for better management.
2. Rule Customization:
- Use AWS Marketplace to find managed rule groups.
- Create rate-based rules to block IPs with excessive requests.
3. Testing and Deployment:
- Use the AWS WAF console to test your rules.
- Deploy the Web ACL to production after thorough testing.
Example Setup
import boto3
client = boto3.client('wafv2')
response = client.create_web_acl(
Name='ExampleWebACL',
Scope='REGIONAL',
DefaultAction={'Allow': {}},
Rules=[
{
'Name': 'SQLInjectionRule',
'Priority': 1,
'Statement': {'SqliMatchStatement': {'FieldToMatch': {'UriPath': {}}, 'TextTransformations': [{'Priority': 0, 'Type': 'NONE'}]}},
'Action': {'Block': {}},
'VisibilityConfig': {'SampledRequestsEnabled': True, 'CloudWatchMetricsEnabled': True, 'MetricName': 'SQLInjectionRule'}
},
# Additional rules can be added here
],
VisibilityConfig={'SampledRequestsEnabled': True, 'CloudWatchMetricsEnabled': True, 'MetricName': 'ExampleWebACL'}
)
print(response)Conclusion
AWS Web Application Firewall WAF is a powerful tool for protecting your web applications from a variety of threats. By understanding its features, setting it up correctly, and maintaining it with best practices, you can ensure robust security for your applications. Whether you are new to AWS WAF or looking to deepen your knowledge, this guide provides a comprehensive overview to help you get started and excel in using AWS WAF.
What tool is used to detect WAF?
Henrique Wiffit (Waf00f), it can detect and fingerprint WAFs. The best thing about this tool is that it is very simple to use and can discover a variety of WAF products (e.g. Profense, Net Continuum, Barracuda, Citrix NetScaler, Mod Security, etc.)
Is WAF hardware or software?
What is WAF code?
A web application firewall (WAF) is an additional security tool for brands to protect against web security threats and common code vulnerabilities like SQL injection attacks, cross-site scripting, and cross-site forgery requests.







