
Which Protocol Traffic does a Web Application Firewall (WAF) Monitor?
Understanding the Scope of Web Application Firewall (WAF) Protocol Monitoring
Introduction to Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) are significant bits of association security framework wanted to safeguard web applications from different online dangers. Not at all like customary firewalls that emphasize network traffic, WAFs explicitly focus on the application layer, where numerous weaknesses live.
By dissecting HTTP and HTTPS traffic, WAFs can identify and hinder pernicious solicitations, for example, SQL infusion, cross-website prearranging (XSS), and other normal web takes advantage of. This proactive methodology assists associations with forestalling information breaks, unapproved access, and margin time brought about by digital assaults. With the rising complexity of digital dangers, the job of WAFs in getting web applications has become vital for organizations across ventures.
Definition and purpose
A Web Application Firewall (WAF) is a security plan that protects web applications from various computerized risks by noticing and controlling drawing closer and dynamic traffic. Not by any stretch of the imagination like standard firewalls, which on a very basic level revolve around network traffic, WAFs work at the application layer, providing granular control over HTTP and HTTPS traffic.
The fundamental job of a WAF is to perceive and ease typical web application shortcomings, for instance, SQL mixture, cross-site setting up (XSS), and other malignant exercises, subsequently protecting delicate information and guaranteeing the honesty and accessibility of web administrations.
Understanding Protocol-Traffic Monitoring with Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) expect a basic part in safeguarding web applications against different modernized chances. These security courses of action are expected to screen, channel, and block harmful traffic wanting to exploit shortcomings in web applications. One of the key assignments performed by WAFs is checking convention traffic to guarantee the uprightness and security of web applications.
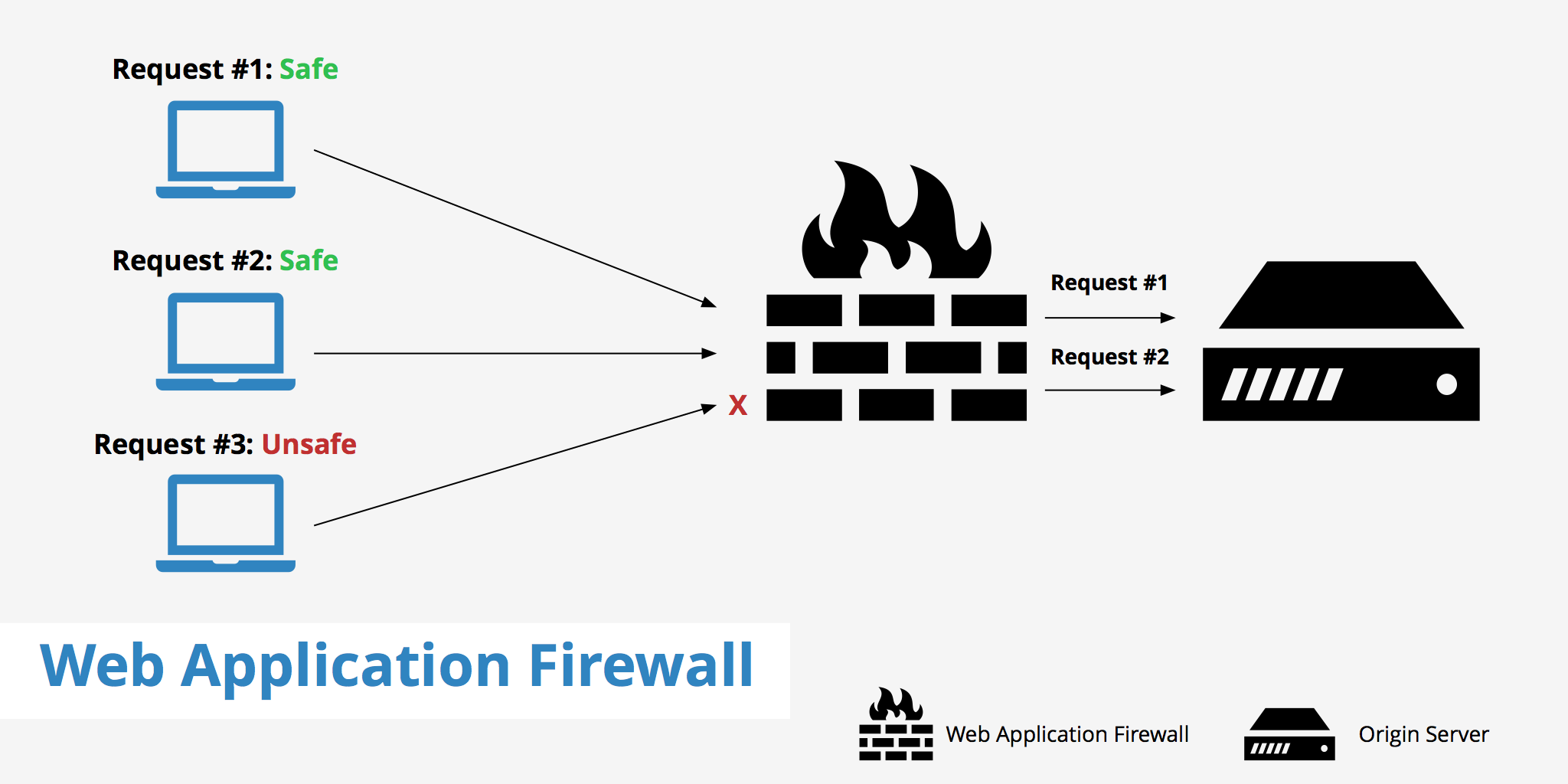
Explanation of protocols
Conventions are a bunch of decisions and norms that oversee information trading between gadgets or frameworks. A couple of shows expect a basic part in working with correspondence among clients and servers concerning web application security.
Generally utilized conventions incorporate HTTP (Hypertext Move Convention) and its solid partner HTTPS, which are liable for sending web content. Also, conventions like FTP (Document Move Convention), SMTP (Straightforward Mail Move Convention), and DNS (Space Name Framework) fill explicit needs in information move, email correspondence, and area goals separately.
Importance of monitoring traffic
Monitoring traffic is vital for ensuring the security and performance of web applications. Associations can progressively recognize and answer potential security dangers by examining approaching and active information bundles.
This proactive methodology mitigates dangers, for example, unapproved access, information breaks, and administration disturbances. Furthermore, traffic observing gives bits of knowledge into application use designs, empowering associations to improve execution and upgrade client experience.

In general, compelling traffic checking is fundamental for keeping up with the honesty, accessibility, and secrecy of web applications in the present dynamic and developing digital danger scene.
How WAFs Monitor Protocol Traffic
WAFs employ sophisticated techniques to monitor different protocols traversing through web applications. These protocols serve as communication standards enabling data exchange between clients and servers. WAFs can progressively identify and moderate potential security gambles by breaking down convention traffic.
Commonly Monitored Protocols by WAFs
HTTP and HTTPS: Hypertext Move Convention (HTTP) and its protected partner HTTPS are among the most regularly checked conventions by WAFs. These conventions work with exchanging web content and client information, making them practical objectives for digital assaults.
FTP: Document Move Convention (FTP) moves records between a client and a server. WAFs screen FTP traffic to forestall unapproved access and information exfiltration.
SMTP: Straightforward Mail Move Convention (SMTP) is answerable for sending and getting messages. WAFs examine SMTP traffic to recognize and obstruct spam, phishing endeavours, and email-based dangers.
DNS: Area Name Framework (DNS) interprets space names into IP addresses, empowering clients to access sites utilizing intelligible addresses. WAFs screen DNS traffic to forestall DNS-based after, for example, store harming and DNS commandeering.
Importance of Monitoring Various Protocols
Effective monitoring of diverse protocols is essential for maintaining the security posture of web applications. Each protocol poses unique security challenges, and overlooking any of them can leave web applications vulnerable to exploitation by cybercriminals.
Security implications
Failing to monitor web application traffic can have severe security implications. Without appropriate oversight, pernicious entertainers can take advantage of weaknesses in web applications, prompting information breaks, monetary misfortunes, and harm to an association’s standing.

In addition, unmonitored traffic builds the gamble of unapproved access, infusion assaults, and malware penetration. By ignoring traffic observation, associations are defenceless against digital dangers, including data burglary, administration disturbances, and consistency infringement.
Consequently, focusing on strong traffic observing measures is fundamental for shielding touchy information and alleviating security gambles.
Potential threats
Cyber threats pose risks to web applications, highlighting the importance of effective traffic monitoring. Common threats include SQL injection, where aggressors exploit weaknesses to control information bases, and cross-webpage prearranging (XSS), empowering assailants to infuse malignant contents into website pages.
Furthermore, DDoS (Disseminated Forswearing of Administration) assaults plan to overpower web servers, causing margin time and administration interruptions. Different dangers incorporate malware contaminations, information breaks, and unapproved access endeavours. By observing traffic, associations can instantly identify and relieve these dangers, lessening the probability of fruitful digital assaults and limiting expected harm.
Factors Influencing Protocol-Traffic Monitoring
Several factors influence the approach to protocol traffic monitoring, including the sort of web application, the organization climate’s intricacy, and the association’s particular security necessities.
Application type
The nature of the web application influences the approach to traffic monitoring. Different applications have unique architectures, functionalities, and security requirements, necessitating tailored monitoring strategies. For instance, e-commerce platforms handling sensitive financial transactions may require more stringent monitoring than informational websites.
Similarly, monitoring requirements vary between web applications hosted on-premises and those deployed in cloud environments. Understanding the specific characteristics and vulnerabilities of each application type enables organizations to implement appropriate traffic monitoring solutions to effectively mitigate risks and ensure the security and availability of their web services.
Network environment
The network environment in which a web application operates greatly influences traffic monitoring requirements. Factors such as network topology, traffic volume, and connectivity options impact the effectiveness of monitoring solutions.
For example, distributed networks spanning multiple locations may require centralized monitoring tools to ensure comprehensive visibility. Additionally, network segmentation and firewall configurations affect traffic flow and accessibility, necessitating adjustments to monitoring strategies.
Understanding the intricacies of the network environment enables organizations to send fitting traffic observing arrangements able to recognize and moderate potential security dangers, hence defending web applications and supporting continuous activities.

Challenges Faced in Protocol-Traffic Monitoring
Despite the significance of protocol traffic monitoring, a few difficulties need to be solved. Scrambled traffic, emerging from the broad reception of HTTPS, represents a test as it disguises vindictive exercises. Besides, complex application models make it hard to decipher convention traffic designs precisely.
Encrypted traffic
Encrypted traffic poses a challenge for traffic monitoring as it conceals malicious activities. With the widespread adoption of HTTPS, associations should utilize progressed decoding strategies to examine scrambled information bundles. The inability to screen scrambled traffic leaves web applications powerless against undetected security dangers.
Complex application architectures
Complex application architectures present challenges for traffic monitoring due to their intricate design and diverse components. Monitoring traffic within such architectures requires comprehensive visibility across all layers and components, ensuring effective detection and mitigation of potential security risks and vulnerabilities.
Strategies for Effective Protocol-Traffic Monitoring
To overcome these challenges, organizations can adopt various strategies, such as leveraging advanced features offered by WAFs, including AI, and conducting examinations. Furthermore, coordinating WAFs with other security instruments like interruption identification frameworks (IDS) and security data and occasion the executive’s (SIEM) arrangements upgrades perceivability and empowers extensive danger location and reaction.
Use of advanced WAF features
Utilizing advanced features offered by web application firewalls (WAFs) improves conventional traffic observing capacities. Elements such as AI calculations, investigation, and granular rule sets empower WAFs to recognize and alleviate modern digital dangers, reinforcing the security stance of web applications.
Case Studies
Several organizations have successfully implemented WAFs for protocol traffic monitoring, enhancing security posture and protection against cyber threats. Case studies illustrate the practical application of WAF technology in mitigating attacks and safeguarding web applications.
Future Trends in WAF Technology
WAF technology continues to evolve rapidly, determined by progressions in network safety dangers and advances. Future patterns incorporate the coordination of artificial brainpower (computer-based intelligence) for proactive danger identification, support for arising conventions, and the reception of cloud-local WAF arrangements.

Conclusion
In conclusion, protocol traffic monitoring with Web Application Firewalls is a basic part of an online protection system for shielding web applications against a horde of dangers. By checking different conventions, associations can moderate dangers, safeguard touchy information, and guarantee the continuous accessibility of web administrations.
How does a WAF monitor protocol traffic?
WAFs inspect protocol traffic using predefined rulesets and social examination procedures to distinguish and relieve potential security gambles.
Why is it essential to monitor diverse protocols with a WAF?
Monitoring diverse protocols ensures extensive insurance against various digital dangers, focusing on web applications.
What are some challenges associated with protocol traffic monitoring?
Challenges include encrypted traffic, complex application designs, and the requirement for persistent updates to control sets.
What future trends can we expect in WAF technology?
Future trends include AI-driven threat detection, support for arising conventions, and the reception of cloud-local WAF arrangements.







